What is Zero Day CVE-2024-3400?
A command injection vulnerability in the GlobalProtect feature of Palo Alto Networks PAN-OS software for specific PAN-OS versions and distinct feature configurations may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. Fixes for PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 are in development and are expected to be released by April 14, 2024. Cloud NGFW, Panorama appliances, and Prisma Access are not impacted by this vulnerability. All other versions of PAN-OS are also not impacted.
How can we mitigate this?
The current solution is to use Threat ID 95187 if you have the Threat Prevention subscription. Instructionson how to do this are available at the link provided https://live.paloaltonetworks.com/t5/globalprotect-articles/applying-vulnerability-protection-to-globalprotect-interfaces/ta-p/340184
How can you check if these security settings are in place?
The vulnerability profile with blocking option of reset-server, resets the TCP connection and blocks the UDP connection.
Now, if you need to verify if this is working, login to your PAN device which has the Global protect gateway. Go to Monitor > Traffic and in the search filter it with the rule name (( rule eq ‘Name-of-security-policy’ ) You should now see logs with type : end | application : incomplete | session end reason : aged out which means that the TCP connection was reset.
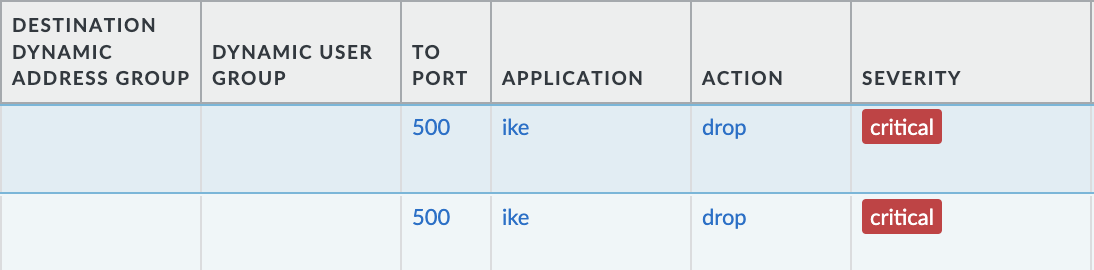
To verify UDP connection go to Monitor > Threat and in the search filter it with the destination zone of the global protect gateway ( zone.src eq ‘Name-of-GP-Zone’ ) and category of threat ( category-of-threatid eq ‘code-execution’ )
You should now see logs with action drop.