Recently, CVE-2024-3400 has emerged as a significant vulnerability affecting Palo Alto devices, raising concerns about the integrity of network security. In response, it’s crucial to not only address the vulnerability but also ensure the effective reset of associated threat IDs. In this blog post, we’ll delve into how to verify the reset of Threat IDs 95187, 95189, and 95191 in Palo Alto devices using Postman, bolstering your network’s defenses against potential exploits.
Understanding CVE-2024-3400 and Associated Threat IDs:
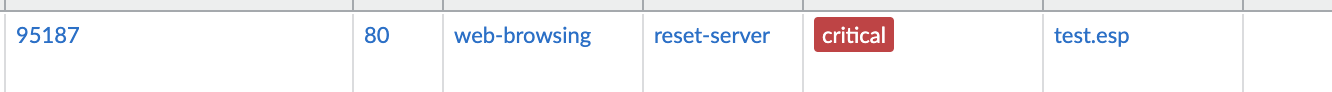
CVE-2024-3400 represents a critical vulnerability in Palo Alto devices, potentially exposing networks to exploitation by malicious actors. Amidst the heightened risk, Threat IDs 95187 (DoS attack detected), 95189 (DDoS attack detected), and 95191 (DNS Amplification Attack detected) are particularly concerning, posing serious threats to network infrastructure and data security.
Verification Process Using Postman:
Here’s a step-by-step guide on how to ensure the reset of Threat IDs 95187, 95189, and 95191 using Postman:
-
Start by authenticating to your Postman application open a new request tab
-
Run a Post request to your PAN URL (your-paloalto-ip/ssl-vpn/test.esp).
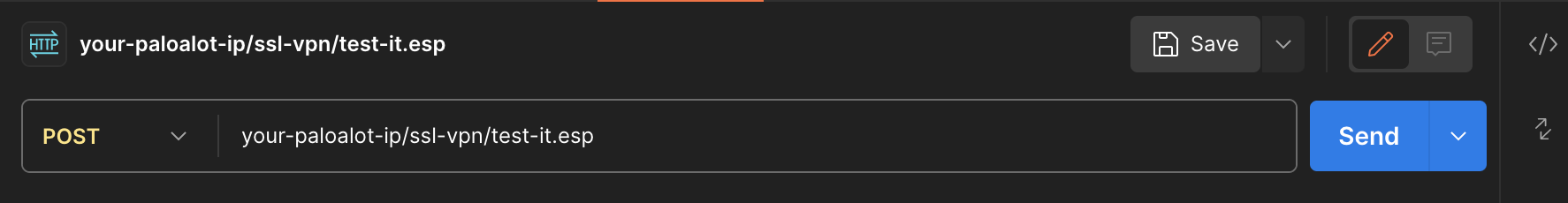
-
Add the following headers as attached
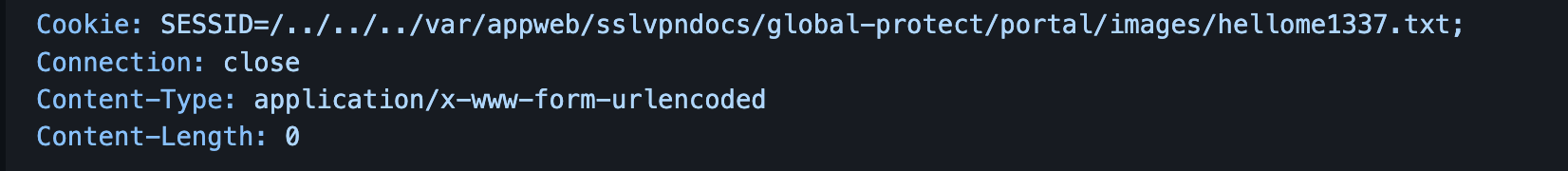
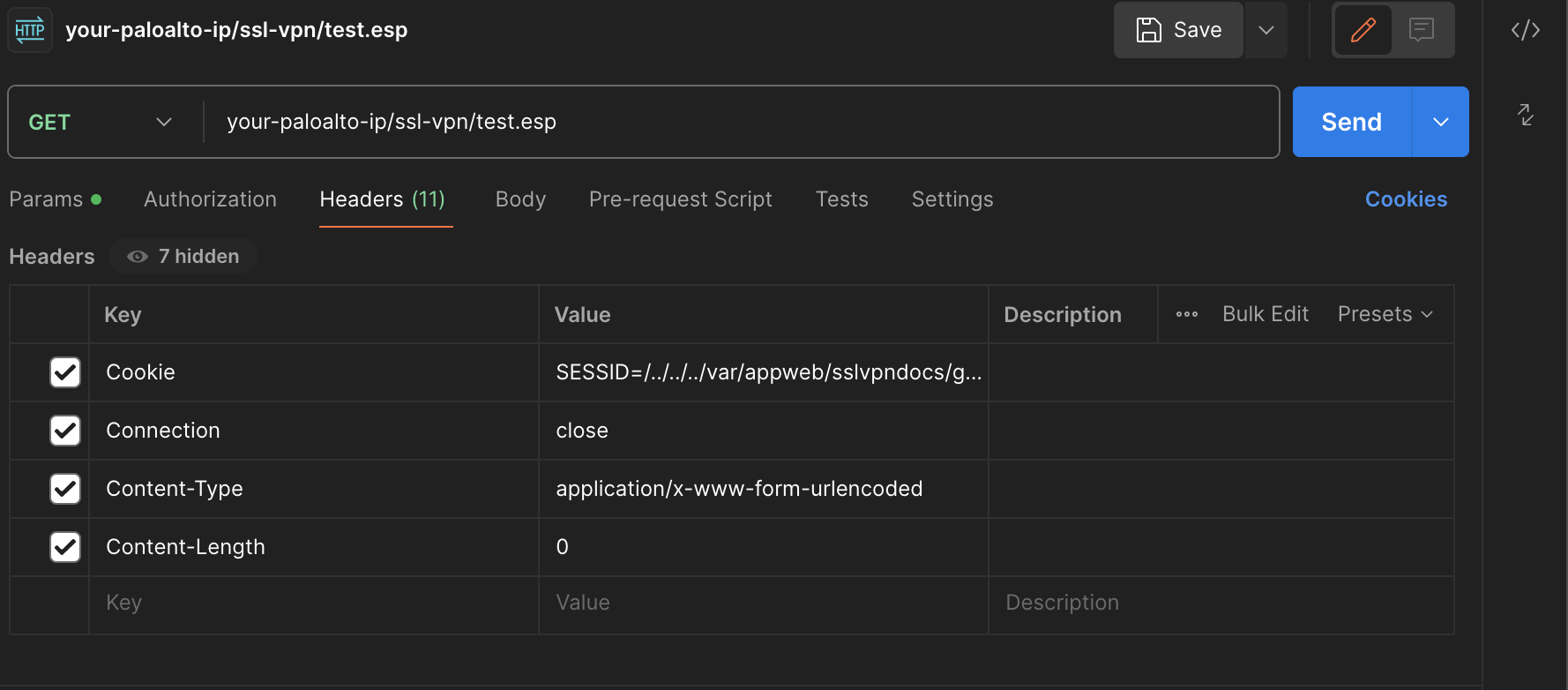
-
Now run the post command to your Palo Alto IP. If the threat ID’s are successfully applied to your Firewall, your post command should be stuck at sending request…
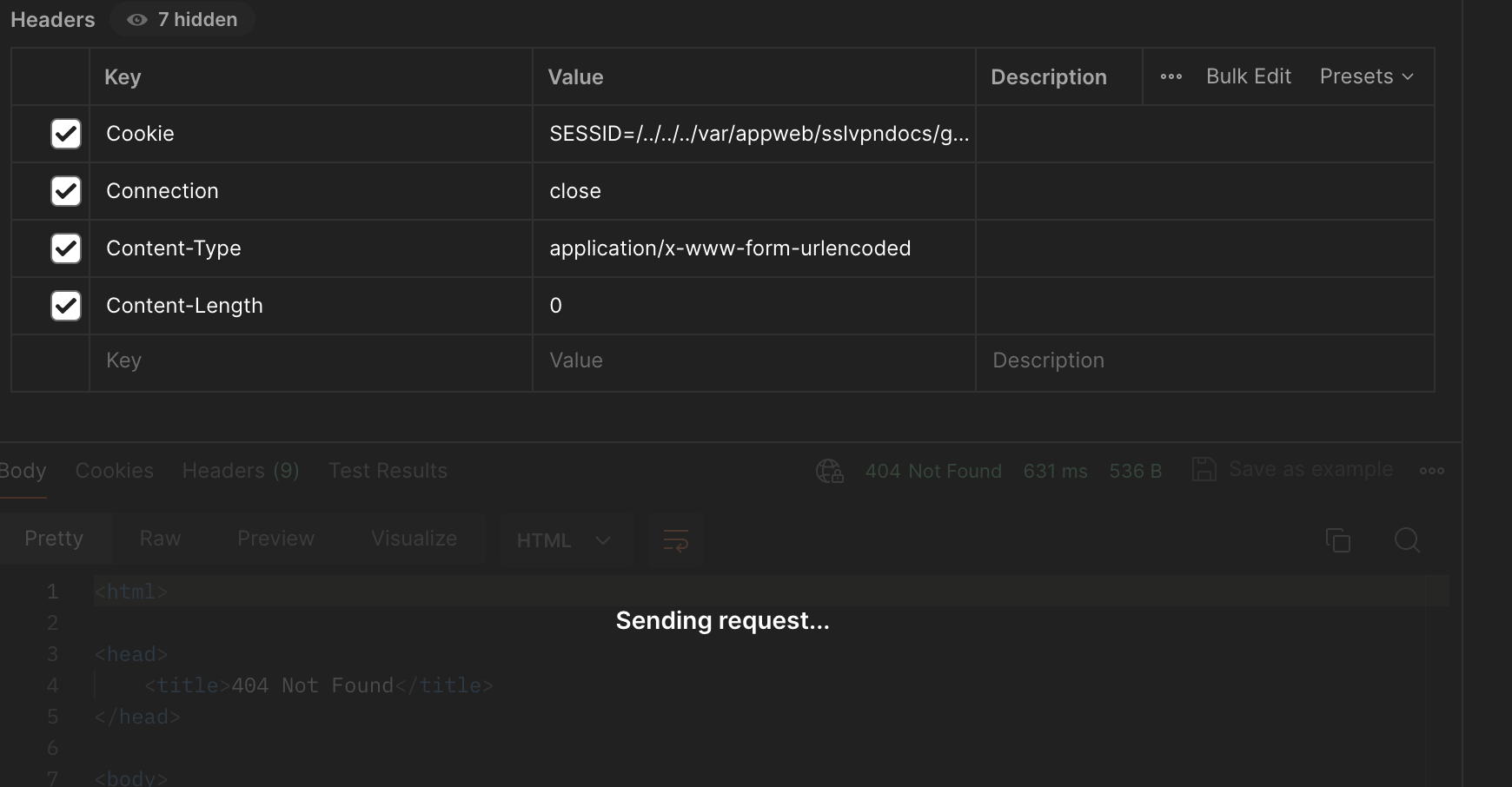
-
In your Firewall you should now have a log for the file name test.esp and action as reset-server.